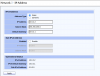
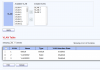
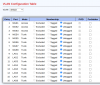
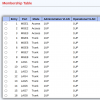
hi, i bought a hasivo network switch and want to set up VLANs but the web interface is confusing to me. this is my first managed switch. before, i only configured subnets on individual physical ports on my firewall (opnsense).
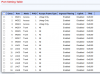
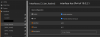
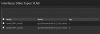
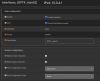
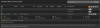
i've searched up tutorials on VLANs and i think i understand the basics of tagging and untagging, but the hasivo interface has so many options and i have no idea what things like "1UP, 3T" on "trunk" vs. "access" that just has "1UP" or administrative vs. operational VLAN mean.
when looking up VLAN / switch config tutorials online it's all just cisco switches using terminal.
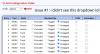
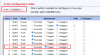
my desired setup for now is to connect the switch to my opnsense using one cable (trunk i guess?), to have one port on the switch which uses the default VLAN so i can always talk to the switch and my opnsense, and then 3 ports which have a non-default VLAN which have their own subnets and firewall rules that i can configure in opnsense so i can isolate these networks.
can someone help me out? i would highly appreciate it
i've searched up tutorials on VLANs and i think i understand the basics of tagging and untagging, but the hasivo interface has so many options and i have no idea what things like "1UP, 3T" on "trunk" vs. "access" that just has "1UP" or administrative vs. operational VLAN mean.
when looking up VLAN / switch config tutorials online it's all just cisco switches using terminal.
my desired setup for now is to connect the switch to my opnsense using one cable (trunk i guess?), to have one port on the switch which uses the default VLAN so i can always talk to the switch and my opnsense, and then 3 ports which have a non-default VLAN which have their own subnets and firewall rules that i can configure in opnsense so i can isolate these networks.
can someone help me out? i would highly appreciate it