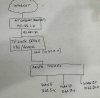
Hi All,
Been pulling my hair out (What's left anyway) for 2 days on this. Hoping to get some expert advice. This isn't my forte so bear with me. I did a quick sketch of the system.
I cannot seem to get the individual VLANS to get access to the internet through the VPN router. Intra routing works fine. VLANS receive IP addresses, can ping from machines across vlans. I can ping all targets from the switch (OS) , vlans to vlans fine everything seems to work as intended with the exception of being able to access the internet. Any help would be much appreciated by me and the family who hasn't seen me for 2 days lol.
Here is the config:
DCS-7050SX-64 running EOS64-4.25.1F
dhcp server
dns server ipv4 192.168.1.254 8.8.8.8
!
subnet 10.62.5.0/24
name Management-DHCP
dns server 10.62.0.1 192.168.1.254
default-gateway 10.62.5.1
range 10.62.5.180 10.62.5.199
!
subnet 10.62.10.0/24
name Physical
dns server 10.62.0.1 8.8.8.8
default-gateway 10.62.10.1
range 10.62.10.180 10.62.10.199
!
subnet 10.62.20.0/24
name Virtual
dns server 10.62.0.1 8.8.8.8
default-gateway 10.62.20.1
range 10.62.20.180 10.62.20.199
!
transceiver qsfp default-mode 4x10G
!
service routing protocols model ribd
!
ip name-server vrf default 192.168.1.254
ip name-server vrf default 8.8.8.8
!
ntp server us.pool.ntp.org
!
spanning-tree mode mstp
!
no aaa root
!
vlan 5
name Management
!
vlan 10
name Physical
!
vlan 20
name Virtual
!
interface Ethernet1
switchport trunk allowed vlan 1,5,10,20
switchport mode trunk
!
interface Ethernet2
!
interface Ethernet3
!
interface Ethernet4
switchport access vlan 5
!
interface Ethernet15
switchport access vlan 5
!
interface Ethernet16
switchport access vlan 10
!
interface Ethernet27
switchport access vlan 10
!
interface Ethernet28
switchport access vlan 20
!
interface Ethernet39
switchport access vlan 20
!
interface Management1
ip address 10.62.2.1/24
!
interface Vlan1
ip address 10.62.0.1/24
!
interface Vlan5
ip address 10.62.5.1/24
dhcp server ipv4
!
interface Vlan10
ip address 10.62.10.1/24
dhcp server ipv4
!
interface Vlan20
ip address 10.62.20.1/24
dhcp server ipv4
ip routing
!
ip route 0.0.0.0/0 10.62.0.1
!
router multicast
ipv4
routing
!
end
Been pulling my hair out (What's left anyway) for 2 days on this. Hoping to get some expert advice. This isn't my forte so bear with me. I did a quick sketch of the system.
I cannot seem to get the individual VLANS to get access to the internet through the VPN router. Intra routing works fine. VLANS receive IP addresses, can ping from machines across vlans. I can ping all targets from the switch (OS) , vlans to vlans fine everything seems to work as intended with the exception of being able to access the internet. Any help would be much appreciated by me and the family who hasn't seen me for 2 days lol.
Here is the config:
DCS-7050SX-64 running EOS64-4.25.1F
dhcp server
dns server ipv4 192.168.1.254 8.8.8.8
!
subnet 10.62.5.0/24
name Management-DHCP
dns server 10.62.0.1 192.168.1.254
default-gateway 10.62.5.1
range 10.62.5.180 10.62.5.199
!
subnet 10.62.10.0/24
name Physical
dns server 10.62.0.1 8.8.8.8
default-gateway 10.62.10.1
range 10.62.10.180 10.62.10.199
!
subnet 10.62.20.0/24
name Virtual
dns server 10.62.0.1 8.8.8.8
default-gateway 10.62.20.1
range 10.62.20.180 10.62.20.199
!
transceiver qsfp default-mode 4x10G
!
service routing protocols model ribd
!
ip name-server vrf default 192.168.1.254
ip name-server vrf default 8.8.8.8
!
ntp server us.pool.ntp.org
!
spanning-tree mode mstp
!
no aaa root
!
vlan 5
name Management
!
vlan 10
name Physical
!
vlan 20
name Virtual
!
interface Ethernet1
switchport trunk allowed vlan 1,5,10,20
switchport mode trunk
!
interface Ethernet2
!
interface Ethernet3
!
interface Ethernet4
switchport access vlan 5
!
interface Ethernet15
switchport access vlan 5
!
interface Ethernet16
switchport access vlan 10
!
interface Ethernet27
switchport access vlan 10
!
interface Ethernet28
switchport access vlan 20
!
interface Ethernet39
switchport access vlan 20
!
interface Management1
ip address 10.62.2.1/24
!
interface Vlan1
ip address 10.62.0.1/24
!
interface Vlan5
ip address 10.62.5.1/24
dhcp server ipv4
!
interface Vlan10
ip address 10.62.10.1/24
dhcp server ipv4
!
interface Vlan20
ip address 10.62.20.1/24
dhcp server ipv4
ip routing
!
ip route 0.0.0.0/0 10.62.0.1
!
router multicast
ipv4
routing
!
end
Attachments
-
777.2 KB Views: 9