I really appreciate you guys troubleshooting this

What is 192.168.0.1? Is it your local real network?
192.168.0.1 is my ISP's router, connected to the WAN port of the OpenWRT router.
OpenWRT is in the DMZ of my ISP router to keep it as dumb as possible.
Is the uplink port defined as a trunk? The uplink port between the router and L3 switch needs to be an access port not a trunk port. An access port will force layer 3. If you are using a trunk port for the uplink then you are using layer 2.
The connection between the switch and the OpenWRT router is trunked, yes.
I haven't declared an uplink port, if that's what you mean.
I know I can define a port as uplink in the VLAN settings of the switch, but I'm not sure what that does.
Should I set this?
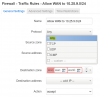
What is the gateway for VLAN100? I think it is working.
Clients in VLAN 100 get 10.25.100.2 as gateway, via option 3 of DHCP.
What does a trace route look like from a client in the VLAN100 network to 9.9.9.9?
Code:
pi@rpi3-sdr:~ $ traceroute -i enxb827eb45a8ec 9.9.9.9
traceroute to 9.9.9.9 (9.9.9.9), 30 hops max, 60 byte packets
1 10.25.100.2 (10.25.100.2) 3.943 ms 3.995 ms 4.566 ms
2 WRT1900AC.lan (10.25.100.1) 3.190 ms 3.077 ms 2.982 ms
3 WRT1900AC.lan (10.25.100.1) 2.906 ms 2.812 ms 2.718 ms
pi@rpi3-sdr:~ $
I agree it is strange this doesn't get stopped at 172.16.1.2... But it works.
@Nikotine - In your brocade config you had 1/1/1 as a mirror port? Is that still there?
Not anymore. Initially I had 1/1/1 as mirror port to 1/1/2, so that I could do some Wireshark analysis on everything going in and out of the switch.
But I removed that when I used 1/1/2 as second link to the OpenWRT router.
Now everything goes via one link via trunked 1/1/1.
Mirroring is still disabled.
This is my config:
Code:
Current configuration:
!
ver 08.0.30tT313
!
stack unit 1
module 1 icx6450-48p-poe-port-management-module
module 2 icx6450-sfp-plus-4port-40g-module
!
global-stp
!
!
!
vlan 9 name main by port
tagged ethe 1/1/1
untagged ethe 1/1/2 to 1/1/36 ethe 1/2/1 to 1/2/4
router-interface ve 9
!
vlan 100 name IPcams by port
tagged ethe 1/1/1
untagged ethe 1/1/37 to 1/1/48
router-interface ve 100
!
vlan 172 name TRANSIT by port
tagged ethe 1/1/1
router-interface ve 172
!
vlan 4095 name DEFAULT-VLAN by port
!
!
!
!
!
aaa authentication web-server default local
aaa authentication enable default local
aaa authentication login default local
default-vlan-id 4095
enable telnet authentication
hostname ICX6450-48P-Router
ip dhcp-client disable
ip dns server-address 172.16.1.2
ip route 0.0.0.0/0 172.16.1.2
!
no telnet server
username root password .....
snmp-server community ..... ro
!
!
clock summer-time
clock timezone gmt GMT+01
!
!
ntp
disable serve
server 10.25.9.1
!
!
web-management https
web-management refresh front-panel 30
web-management session-timeout 3600
!
!
!
interface ethernet 1/1/37
inline power priority 1 power-by-class 3
!
interface ve 9
ip address 10.25.9.2 255.255.255.0
!
interface ve 100
ip address 10.25.100.2 255.255.255.0
!
interface ve 172
ip address 172.16.1.1 255.255.255.0
!
!
!
!
!
!
!
!
!
end