Not getting around the DNS lookup stuff.
Intended client can't find the ADDC.
This is not even covered by any of the tutorials, not as simple as this should be anyways.

Intended client can't find the ADDC.
This is not even covered by any of the tutorials, not as simple as this should be anyways.
Tried added a forward in my firewall to cope with this but it is not working or is the wrong thing or whatever...Note: This information is intended for a network administrator. If you are not your network’s administrator, notify the administrator that you have received this information, which has been recorded in the file C:\WINDOWS\debug\dcdiag.txt.
The following error occurred when DNS was queried for the service location (SRV) resource record used to locate an Active Directory Domain Controller (AD DC) for domain “wsrvaddc1.homered.conram.it”:
The error was: “DNS name does not exist.”
(error code 0x0000232B RCODE_NAME_ERROR)
The query was for the SRV record for _ldap._tcp.dc._msdcs.wsrvaddc1.homered.conram.it
Common causes of this error include the following:
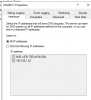
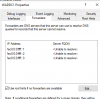
192.168.1.1
- The DNS SRV records required to locate an AD DC for the domain are not registered in DNS. These records are registered with a DNS server automatically when an AD DC is added to a domain. They are updated by the AD DC at set intervals. This computer is configured to use DNS servers with the following IP addresses:
wsrvaddc1.homered.conram.it
- One or more of the following zones do not include delegation to its child zone:
homered.conram.it
conram.it
it
. (the root zone)
Code:
forward-zone:
name: "wsrvaddc1.homered.conram.it."
forward-addr: 192.168.1.42
Last edited: