Hi Guys
Okay the mystery deepens, I can see that my Windows DHCP server is issuing IP addresses to the Intel 40G link cables, but the card within the OS does not acknowledge that the leases has been issued, as it only shows an AutoIP.

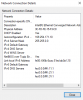
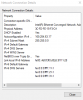
I have confirmed that the switch is linking at 40G to the card on both ports
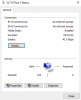
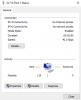
Current configuration:
!
ver 08.0.30uT7f3
!
stack unit 1
module 1 icx6610-48p-poe-port-management-module
module 2 icx6610-qsfp-10-port-160g-module
module 3 icx6610-8-port-10g-dual-mode-module
stack disable
!
global-stp
!
!
!
vlan 1 name DEFAULT-VLAN by port
router-interface ve 1
spanning-tree 802-1w
!
!
!
!
!
aaa authentication web-server default local
aaa authentication enable default local
aaa authentication login default local
enable aaa console
fast port-span exclude ethe 1/2/1 ethe 1/2/6
hostname brocade-sw
ip dhcp-client disable
ip dns domain-list bozzy.info
ip dns server-address 192.168.10.15 192.168.10.16
ip route 0.0.0.0/0 192.168.10.1
!
no telnet server
username admin password .....
!
!
clock timezone gmt GMT+02
!
!
ntp
disable serve
server 192.168.10.1
!
!
web-management https
web-management refresh port-statistic 10
web-management refresh stp 10
web-management refresh tftp 10
web-management refresh rmon 10
web-management frame bottom
web-management page-size 20
!
!
router rip
!
!
!
!
!
!
!
interface ethernet 1/2/1
no spanning-tree
no flow-control
!
interface ethernet 1/2/6
no spanning-tree
no flow-control
!
interface ethernet 1/3/1
speed-duplex 10G-full
!
interface ethernet 1/3/2
speed-duplex 10G-full
!
interface ethernet 1/3/3
speed-duplex 10G-full
!
interface ethernet 1/3/4
speed-duplex 10G-full
!
interface ethernet 1/3/5
speed-duplex 10G-full
!
interface ethernet 1/3/6
speed-duplex 10G-full
!
interface ethernet 1/3/7
speed-duplex 10G-full
!
interface ethernet 1/3/8
speed-duplex 10G-full
!
interface ve 1
ip address 192.168.10.7 255.255.255.0
!
!
!
!
!
!
!
!
!
end
This is the current switch config. I know a lot of you will say that I should have gotten a Mellanox card, but I prefer to use Intel NICs. Also, just a note that this XL710 is a Dell OEM model, obviously used in a Dell PowerEdge server, along with Dell 3M QSFP DAC cables, so i think there shouldnt be any compatibility issues.
Any thoughts or resolution would be appreciated





