On the serious note, it's a pretty serious issue. @fohdeesha sure did A LOT of work to update the first post and make awesome documentation to avoid this but it's true this thread is pretty difficult to follow even with the search results with so many people in between question and answer asking and answering something else."I'm just going to jump into this 320+ page thread with thousands of posts and not bother reading the OP." - Too Many People.
Drag to reposition cover
Brocade ICX Series (cheap & powerful 10gbE/40gbE switching)
- Thread starter fohdeesha
- Start date
Notice: Page may contain affiliate links for which we may earn a small commission through services like Amazon Affiliates or Skimlinks.
I read the OP and this and know how to set up the device via TFTP. I dont see where any config guide is listed on how to set up L3, VLANs, etc. I checked Resources --> Getting Started, --> How-to Guides, --> Reference Materials and dont see any config guide."I'm just going to jump into this 320+ page thread with thousands of posts and not bother reading the OP." - Too Many People.
Anyway, thanks for the help.
Serious question, where is the documentation?? Asking after spending much time trying to find it first. If there is a document that I can read and follow, I'll spend the time doing it. If it is between 320 pages of back and forth forum posts, no one has that kind of time, Brocade is not for me and I'll keep it moving.On the serious note, it's a pretty serious issue. @fohdeesha sure did A LOT of work to update the first post and make awesome documentation to avoid this but it's true this thread is pretty difficult to follow even with the search results with so many people in between question and answer asking and answering something else.
Last edited:
All the ruckus switch manuals are on the manufacturers website, for example Technical Documents | Ruckus Wireless Support
This thread handily condenses some of those technical documents into an easily digestible OP that deals with initial config.
This thread handily condenses some of those technical documents into an easily digestible OP that deals with initial config.
Literally the first post, linked at "Setup / Config / Licensing Guide v2"
Honestly it's not for you. Get a Netgear or something that's plug and play.
Master ZIP (Firmware, Manuals, Licenses)
Honestly it's not for you. Get a Netgear or something that's plug and play.
I read the OP and this and know how to set up the device via TFTP. I dont see where any config guide is listed on how to set up L3, VLANs, etc. I checked Resources --> Getting Started, --> How-to Guides, --> Reference Materials and dont see any config guide.
Anyway, thanks for the help.
Serious question, where is the documentation?? Asking after spending much time trying to find it first. If there is a document that I can read and follow, I'll spend the time doing it. If it is between 320 pages of back and forth forum posts, no one has that kind of time, Brocade is not for me and I'll keep it moving.
Brocade is like HPE in that you define a VLAN, then enter the VLAN and tag or untag ports to it. This is the opposite of Cisco, where you define a VLAN, then enter the port and add your VLANs there
Brocade example:
Code:
SSH@core(config)#vlan 100
SSH@core(config-vlan-100)#tag ethernet 1/1/39Edit: I am wrong, just double checked and the syntax for a VLAN range selection is:
Code:
SSH@core(config)#vlan 1 4 6 10
SSH@core(config-mvlan-1*10)#
Code:
SSH@core(config)#vlan 1 to 10
SSH@core(config-mvlan-1-10)#Brocade indexing starts at 1, so the notation for 1/1/39 is: Stack Unit 1, Module 1, Port 39. Even unstacked, it will always be this notation.
Cisco example:
Code:
core-40g#conf t
core-40g(config)#vlan 100
core-40g(config-vlan-100)#name Test
core-40g(config-vlan-100)#interface int range gi 1/0/1-22
core-40g(config-if-range)#switchport mode trunk
core-40g(config-if-range)#switchport trunk allowed vlan 2,4-6,100In this example, I am able to grab a range of interfaces and tag all the necessary VLANs to them in one shot.
Inter-VLAN routing: The Short Version
Image I knocked together for another post related:
And here are some absolutely barebones L3 inter-VLAN routing config with DCHP helper statements. May or may not work, I have been too busy to lab this out and validate it completely, but it's incredibly similar to a config I had on a Cisco switch before I flattened my network:
Modify a VLAN and define a VE:
Code:
conf t
VLAN 1
router-interface ve 1
int ve 1
ip address 192.168.1.1 255.255.255.0
end
Code:
conf t
ip route 0.0.0.0/0 172.31.255.1
end
Code:
conf t
int ve 1
ip helper-address 1 172.31.255.1
int ve 2
ip helper-address 1 172.31.255.1
< ... and so on ... >
endIf you've never configured an enterprise grade switch before, then this will be an experience because VLANs and routing (ignoring even fancier stuff like iBGP or OSPF) are potential headscratchers when starting from nothing ("Wait, was that interface tagged or untagged? Is the client device tagging a VLAN? Did I forget to include that VLAN in my trunk? Is my subnet prefix the correct size? Did I set the wrong prefix in the route?") The manuals from the Rucksu/Commscope site or packaged in Fohdeesha's ZIP assume that you have a passing familiarity with the concepts.
Last edited:
You literally linked to my page with the zip of all brocade manuals lolI read the OP and this and know how to set up the device via TFTP. I dont see where any config guide is listed on how to set up L3, VLANs, etc. I checked Resources --> Getting Started, --> How-to Guides, --> Reference Materials and dont see any config guide.
Anyway, thanks for the help.
Serious question, where is the documentation?? Asking after spending much time trying to find it first. If there is a document that I can read and follow, I'll spend the time doing it. If it is between 320 pages of back and forth forum posts, no one has that kind of time, Brocade is not for me and I'll keep it moving.
I don't know man.OK, to be fair, I did just go back and check that "Advanced" section of the docs and VLANS and Inter-VLAN routing are both "Coming soon" placeholders.
Still in the first post
covers VLAN basics, inter-VLAN routing, LACP, ACLs.
People want a one-stop shop of all docs, the master ZIP contains documentation straight from Brocade/Ruckus/Commscope. "Oh, it's too detailed, can someone summarize for me?" Terry Henry's videos do that. "I want a summarized document, not a short video." Can't win.
There is literally a PDF titled "fastiron-*-l3guide.pdf / Layer 3 Routing Configuration Guide." It starts with ARP and ends with Multi-VRF. The command reference is just one among many documents.The manuals from the Rucksu/Commscope site or pacakged in Fohdeesha's ZIP assume that you have a passing familiarity with the concepts. The manufacturer's documentation is not going to have a full "here's how you go form first start to routed VLAN" example; it's mostly a command reference that will have specific, basic examples of a given command.
Honestly a lot of that is out of my comfort zone but it serves as a great starting point. The documents provide a good starting foundation. Isn't this what "homelab" is all about? Self learning and initiative? If someone wants to be spoonfed they can get a support contract and ask the vendor directly. Otherwise it's slogging through threads like this one.
Sorry for sounding like an asshole.
@klui: I haven't re-read the OP or the checked the ZIP since before his big V2 update, so my bad. That is an extremely comprehensive doc set (just downloaded it).
And no, you don't sound like an asshole, at least to me. I did read this whole thread back when I first encountered it, took a few days (I think it was sub 200 pages when I first found it?) and I was wanting to get into 10G networking and retire my Cisco 2960S.
That L3 guide (I scrolled through the IPv4 and IPv4 Static Routing sections) should give anyone with a basic understanding of routing and subnetting enough information to piece together a working config, at least on the switch side.
The most common error I see in setting up routed VLANs is that people forget to put reverse routes on the firewall/router upstream and wonder why the internet doesn't work.
And no, you don't sound like an asshole, at least to me. I did read this whole thread back when I first encountered it, took a few days (I think it was sub 200 pages when I first found it?) and I was wanting to get into 10G networking and retire my Cisco 2960S.
That L3 guide (I scrolled through the IPv4 and IPv4 Static Routing sections) should give anyone with a basic understanding of routing and subnetting enough information to piece together a working config, at least on the switch side.
The most common error I see in setting up routed VLANs is that people forget to put reverse routes on the firewall/router upstream and wonder why the internet doesn't work.
Last edited:
My eyes totally skipped over that. FMLLiterally the first post, linked at "Setup / Config / Licensing Guide v2"
Master ZIP (Firmware, Manuals, Licenses)
Honestly it's not for you. Get a Netgear or something that's plug and play.
All good brother. I am looking at that one right now. "fastiron-08030mb-l3guide.pdf"There is literally a PDF titled "fastiron-*-l3guide.pdf / Layer 3 Routing Configuration Guide." It starts with ARP and ends with Multi-VRF. The command reference is just one among many documents.
Honestly a lot of that is out of my comfort zone but it serves as a great starting point. The documents provide a good starting foundation. Isn't this what "homelab" is all about? Self learning and initiative? If someone wants to be spoonfed they can get a support contract and ask the vendor directly. Otherwise it's slogging through threads like this one.
Sorry for sounding like an asshole.
Very helpful post. Thank you LR.Brocade is like HPE in that you define a VLAN, then enter the VLAN and tag or untag ports to it. This is the opposite of Cisco, where you define a VLAN, then enter the port and add your VLANs there
we just a big ole happy switching family
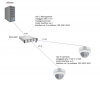
I am planning to use the ICX6450-24P for a about 12-16 IP cameras isolated and not connected to the internet. Going to have ethernet cable connected from a pfSense box to the switch for management only and looking for the ICX6450 to handle all the routing with the cameras.
So I checked the config guide, fastiron-08030mb-l3guide.pdf.
correct me if I am wrong but the guide says IP routing is on by default. I dont believe I will need DHCP, going to use static addresses for the cameras. Therefore, I believe all I would need to do is configure VLANs and I would be good to go.
Does that sound correct? This would be my first L3 switch, never configured an L3 before. It's probably very obvious, lol.
So I checked the config guide, fastiron-08030mb-l3guide.pdf.
correct me if I am wrong but the guide says IP routing is on by default. I dont believe I will need DHCP, going to use static addresses for the cameras. Therefore, I believe all I would need to do is configure VLANs and I would be good to go.
Does that sound correct? This would be my first L3 switch, never configured an L3 before. It's probably very obvious, lol.
Last edited:
You are correct, I wasn't thinking of the scenario where the management VLAN would need to access both the ICX6450 and the cameras but prevent Camera VLAN from talking to the Management VLAN.IP routing feature is enabled but you still need to configure everything on your VE(s) per the guide if cameras need to talk to devices outside their VLANs.
Am I on the right path?
#Create VLANs
Code:
vlan 2 Management
untagged ethe 1/1/1
router-interface ve 2
interface ve 2 ip address 192.168.2.2/24
vlan 3 Cameras
untagged ethe 1/1/2 to 1/1/24
router-interface ve 3
interface ve 3 ip address 192.168.3.2/24
Code:
ip access-list extended "Block inbound"
deny ip any any
interface ve 2 ip access-group "Block inbound" inI just ordered an 6450-24P off eBay.
I was a bit confused on reading the ACL implementation. Wouldn't "deny ip any any" assigned to ve2 deny any inbound traffic to the management interface from any IPs?
From what I read, inbound ACLs on VEs apply to traffic going IN to the VE from the VLAN to which the VE is assigned.
I believe the issue with using that is that it cannot access the regular network channels/ports. I still need to be able to access the Camera VLAN 3 to configure the cameras and NVR.
I think I may have figured out a better solution, just make VLAN 2 the management VLAN for security purposes. I dont think I would need ACLs. I believe no other VLANs can access the Management VLAN by definition.
vlan 2 Management
untagged ethe 1/1/1
management-vlan
router-interface ve 2
interface ve 2 ip address 192.168.2.2/24
I was a bit confused on reading the ACL implementation. Wouldn't "deny ip any any" assigned to ve2 deny any inbound traffic to the management interface from any IPs?
From what I read, inbound ACLs on VEs apply to traffic going IN to the VE from the VLAN to which the VE is assigned.
you referring to the out-of-band-management port, below the console port?I would not waste a regular port for management when there is a dedicated management port on the switch.
I believe the issue with using that is that it cannot access the regular network channels/ports. I still need to be able to access the Camera VLAN 3 to configure the cameras and NVR.
I think I may have figured out a better solution, just make VLAN 2 the management VLAN for security purposes. I dont think I would need ACLs. I believe no other VLANs can access the Management VLAN by definition.
vlan 2 Management
untagged ethe 1/1/1
management-vlan
router-interface ve 2
interface ve 2 ip address 192.168.2.2/24

I've not implemented ACLs but your original post just seems wrong. Blocking the VE basically prevents you from connecting to your switch. Look at Terry Henry's videos about that as there is precedence for ACLs. It's in the first post.
What I see is you're using the management interface to access user data and that goes against the concept of an OOB management network. Of course it's your network and you can probably get it to work.
What I see is you're using the management interface to access user data and that goes against the concept of an OOB management network. Of course it's your network and you can probably get it to work.
Yep, viewed those video prior to that post. I see what you mean by blocking the VE. I guess I could either block inbound on ve 2 or block outbound on ve 3. However, it probably makes more sense to block incoming on ve 2.
#Create VLANs
#Block access to management VLAN
#Create VLANs
Code:
vlan 2 Management
untagged ethe 1/1/1
router-interface ve 2
interface ve 2 ip address 192.168.2.2/24
vlan 3 Cameras
untagged ethe 1/1/2 to 1/1/24
router-interface ve 3
interface ve 3 ip address 192.168.3.2/24
Code:
ip access-list extended "Block inbound to Management"
deny ip 192.168.3.0/24 192.168.2.0/24
interface ve 2 ip access-group "Block inbound to Management" in