Suggest we start from the very beginning, it's a very good place to start.
VLANs are your layer 2 segmentation - a subnet must be wholly contained within a VLAN, as the subnet operates at layer 3. They can be port based VLANs, where a specific port on a layer 2 switch is assigned to a particular VLAN, or tagged, where the endpoint can select which VLAN to use for traffic (but which is still controlled by the list of permitted VLANs on the layer 2 switch).
Note that unmanaged switches are effectively layer 1 devices and so whatever configuration you assign to the smarter switch port applies to all the "dumb" switch ports.
It sounds to me like you want the two APs to be on an isolated VLAN, which you've defined as VLAN 5. That's fine, the numbers are arbitrary. I would recommend that you troubleshoot by using a pair of wired devices to ensure they communicate OK. In Cisco speak, a port-based VLAN with no smarts on the end device is usually configured as switchport mode access; switchport access vlan 5. The endpoint device cannot "escape" VLAN 5.
As for the connection to your Sophos, it sounds like you're using a single cable to carry more than 1 VLAN. Again, no problem. IIRC (this is the end of my Cisco knowledge) a port in General mode will have a native VLAN and also accept tagged packets - so one device with a single physical cable can be on multiple VLANs with appropriate IP addresses. A trunk port, however, expects all packets to be already tagged to a VLAN (someone can correct me if I'm wrong here). Your general port will accept tagged packets on permitted VLANs, and any untagged packets will be tagged and untagged as needed by the switch; those "untagged" packets will be on the native VLAN.
Normally we don't use VLAN1, because packets specifically on VLAN1 are indistinguishable from those not tagged (as I undserstand it anyway). So a device on VLAN1 can potentially hop VLANs - which is a security risk. Also, you mentioned that you configured Sophos with VLAN 10, but your APs are on VLAN 5. I think this might illustrate part of what's going wrong.
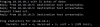
So here's what my stab in the dark switch config might look like - I don't have a Cisco handy to check syntax but I trust it will suffice for you:
Sophos on port 2
AP1 on port 3
AP2 on port 4
interface gi0/2
switchport mode general
switchport general pvid 1
switchport general allowed vlan add 5 tagged
spanning-tree portfast
end
interface gi0/3
switchport mode access
switchport access vlan 5
spanning-tree portfast
end
interface gi0/4
switchport mode access
switchport access vlan 5
spanning-tree portfast
end
Your Sophos needs an interface on VLAN 1 (Eth0?) and a tagged interface on 5 (note it matches) - configure your IP addressing and rules appropriately.
Now as for DHCP, you'll need to do one of two things:
* Configure DHCP forwarding (DHCP Helper) on Sophos to forward DHCP from VLAN 5 to the DHCP server on VLAN 1, confgure a scope for VLAN 5 on the DHCP server;
* Configure Sophos as DHCP server for VLAN 5.
Hope this helps.