@coxhaus : Thank you. However, maybe you missed the post I quoted from
@StammesOpfer. Like
@Vesalius answered, pfSensecannot be a DHCP server for a subnet that it has no interface on it (either by defining the VLAN interfaces or by adding dedicated NICs for the VLANs).
Also, as I said in my post, for the immediate time, I cannot afford running a dedicated DHCP server.
@Vesalius : VLAN 5 and 40 do not need internet access. The backup server has a second interface that will be unplugged and that I will set to VLAN 10 whenever I need it to be online for maintenance and updates.
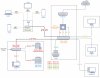
The limitation I have is the SG-350 because it only has 10 ports. On pfSense, with my setup, I still have one spare port on pFsense, eventually two if I take VLAN50 out of internet. I can also gain 1 port on the SG350 by adding a simple VLAN aware switch to join the two VLAN 50 TVs.
I still have a few questions:
1- Having a trunk from SG350 Switch to Pfsense with the VLANs is a no go for downstream traffic routing issues as I understood. However, no one mentioned this: With the VLANs defined on pfSense + Firewall rules to disable any routing between the interfaces in pfSense, will the downstream traffic still cause routing issues at the pfSenseLevel ? That way, L3 switch can do the interVLAN routing and pfSense runs on-a-stick with a trunk to the switch !
2- With my diagram, does pfSense block by default any routing between the physical interfaces because they are on different subnets ?
3- With my diagram, do I still need to define the VLANs in pfSense and assign them to the physical interfaces ? If not, will pfSense remove the VLAN tags causing downstream traffic issues at the Switch ingress level ?
4- In my diagram, I put pfSense in the VLAN 20 IP range, same as the Switch it is connected to. Is it a a good choice or should it be on its own VLAN or IP subnet ?
I am new to VLANs and some concepts are not clear, despite the huge reading I did in the last months.
Thank you for your help setting this up.
Just the first step...