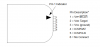
Yeah, there are a number of serial, ISP, JTAG and SWD headers. The DiagOS also contains a lot of pin mappings and GPIO bit-bang interfaces to access the PIC and CPLD.
As an aside: VMware SD-WAN 5.0 - 软件定义的 WAN - sysin | SYStem INside | 软件与技术分享 seems to have a dump of all the packages, including the VMWare image for the Edge 6x0 (so 600 and 610), but of course they uploaded it to a 'Baidu network disk' with a password on it. The filenames and hashes do match with what VMWare is showing, so that is at least correct, but I don't know where to get the files so far.
In theory, they should also have the updates for all the firmware blobs, even Dell support chat refers to them... (which is really weird, since Dell makes those firmwares)
I'm imaging the eMMC for starters so everyone can at least have a working DiagOS, but I don't know how to get the CPLD, it appears the JED files are missing in the DiagOS, but vmetool (which is used to update the code) is present. It can't read from the CPLD, but that might simply be because the program can't do it. Another option is the lock bit is set on the CPLD and thus we cannot read it out.
As an aside: VMware SD-WAN 5.0 - 软件定义的 WAN - sysin | SYStem INside | 软件与技术分享 seems to have a dump of all the packages, including the VMWare image for the Edge 6x0 (so 600 and 610), but of course they uploaded it to a 'Baidu network disk' with a password on it. The filenames and hashes do match with what VMWare is showing, so that is at least correct, but I don't know where to get the files so far.
Code:
VMware SD-WAN Edge Upgrade Package (for Edge 500, 510, 510-LTE, 5X0, and 6X0)
File size: 190.56 MB
File type: zip
Name: edge-imageupdate-EDGE5X0-x86_64-5.1.0.2-5827-R5102-20230310-GA-6ee0ca8b2d.zip
Release Date: 2023-03-14
VMware SD-WAN Edge Upgrade Package (for Edge 500, 510, 510-LTE, 5X0, and 6X0)
This is a software upgrade for the VMware SD-WAN Edge that is deployed on-premise in Datacenter/Bran ch sites. This upgrade package is for Edge models 500, 510, 510-LTE, 5X0, and 6X0.
MD5SUM: 81f3c6b51c7df35440c56e0eae36eb92
SHA1SUM: 94dbb4e1e04880e23cd912925d0a8e74f57be47d
SHA256SUM: d7477639dffa14c2f316c68a824301002918bf2e46fddad94fc9e60f647f0a6dIn theory, they should also have the updates for all the firmware blobs, even Dell support chat refers to them... (which is really weird, since Dell makes those firmwares)
I'm imaging the eMMC for starters so everyone can at least have a working DiagOS, but I don't know how to get the CPLD, it appears the JED files are missing in the DiagOS, but vmetool (which is used to update the code) is present. It can't read from the CPLD, but that might simply be because the program can't do it. Another option is the lock bit is set on the CPLD and thus we cannot read it out.
Last edited: