After lurking here and elsewhere for a while I've decided to pull the trigger and do a home network overhaul with a sprinkling of 10g.
Main equipment is Aruba S2500, SMC 8708L2, Netgear GS108Ts and an underused pfSense box from old setup, Mellanox cards
Some things I have been considering:
So what I'm thinking is reconfigure existing bare metal pfSense to Proxmox with 10g card, LXC/Dockers for pfSense/native vpn app/Omada app/ and piHole(s) for DNS and DHCP (separated by vlan). This way, if I change VPN provider or VPN provider changes protocol/servers all I have to do is change app. Repupose small 8 port switch for OOB. (orange is 10G)
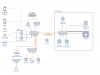
Main equipment is Aruba S2500, SMC 8708L2, Netgear GS108Ts and an underused pfSense box from old setup, Mellanox cards
Some things I have been considering:
- openVPN is slow
- VPNs seem to be fastest on native app (which needs updated periodically) followed by integration with routers/openWRT
- pfSense wireguard has gone from botched to experimental but no direct support by any vpn host like openWRT
- piHole has a slick/easy interface but that goes out the window with a bunch of chatty IoT devices clogging the logs etc
- firewall on stick is recommended for LAN wirespeed routing BUT I'm not sure I've seen anyone feed a pfSense box 2x10g bond from the switch
- OOB management
So what I'm thinking is reconfigure existing bare metal pfSense to Proxmox with 10g card, LXC/Dockers for pfSense/native vpn app/Omada app/ and piHole(s) for DNS and DHCP (separated by vlan). This way, if I change VPN provider or VPN provider changes protocol/servers all I have to do is change app. Repupose small 8 port switch for OOB. (orange is 10G)


