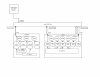
I've been having fun reconfiguring my home network the past few days and have hit a few issues. The basic setup is:
As it stands, DHCP for vlan1 and routing to the outside world are still being done by my Vigor 2925 router which has its WAN port directly connected to the cable modem and receives its WAN address via DHCP. I'm testing setting up DHCP and routing on the PFSense VM in the vlan30 as a proof of concept which won't disturb any importantcurrently-running services.
What works:
Which makes me think there's a problem with the bridging setup on the PVE hosts. As I understood it, the bridges are essentially L2 devices so I shouldn't need to set up any routes on the PVE hosts. If anyone can point me towards how I might further debug my current issues, I'd be extremely grateful.
Host bridging, vlan and bonding set up as per: Network Model - Proxmox VE
magnificat interfaces file:
netcat's interfaces
- vlan1 - all trusted "client" traffic for the time being 192.168.0.0/24
- vlan10 - separate network for proxmox corosync/clustering 192.168.1.0/24
- vlan30 - traffic that needs to go out via a VPN 192.168.30.0/24
- vlan50 - guest wifi 192.168.0.50/24
- vlan200 - NFS storage between proxmox hosts and freenas guests 192.168.200.0/24
- vlan99 - means of connecting the cable modem WAN to the pfsense vm
- netcat - proxmox VE 5 host connected to switch via a 1gb bond and a 10gb bond
- magnificat - pve 5 host connect via 1gb bond
As it stands, DHCP for vlan1 and routing to the outside world are still being done by my Vigor 2925 router which has its WAN port directly connected to the cable modem and receives its WAN address via DHCP. I'm testing setting up DHCP and routing on the PFSense VM in the vlan30 as a proof of concept which won't disturb any importantcurrently-running services.
What works:
- PVE hosts (netcat and magnificat) can see each other fine and dandy in both vlan1, vlan30 and vlan10, proxmox clustering is happy
- Other devices in vlan1 can connect to both the PVE hosts
- Both PVE hosts can connect to the FreeNAS VM via vlan200 or vlan1 and have mounted NFS shares
- devices in vlan1 can connect to FreeNAS
- kitekat container on magnificat can connect to outside world via vlan1 and devices in vlan1 can connect to it (ssh, plex)
- devices in vlan1 can connect to the pfSense VM via its LAN interface (ssh, web)
- magnificat (PVE host) nor its containers can ping the pfsense's OPT1 vlan30 address (but netcat and the switch can)
- pfsense is running a dhcp server on the opt1 vlan30 interface but dhclient in kitekat gets nothing (so I've set it statically for now).
- the arp table on the pfsense box contains entries for the switch, itself, both the pve hosts (all ping-able), and kitekat (not pingable)
- kitekat cannot ping the switch in vlan30 (but can reach both the pve hosts in vlan30)
Which makes me think there's a problem with the bridging setup on the PVE hosts. As I understood it, the bridges are essentially L2 devices so I shouldn't need to set up any routes on the PVE hosts. If anyone can point me towards how I might further debug my current issues, I'd be extremely grateful.
Host bridging, vlan and bonding set up as per: Network Model - Proxmox VE
magnificat interfaces file:
Code:
# network interface settings; autogenerated
# Please do NOT modify this file directly, unless you know what
# you're doing.
#
# If you want to manage part of the network configuration manually,
# please utilize the 'source' or 'source-directory' directives to do
# so.
# PVE will preserve these directives, but will NOT its network
# configuration from sourced files, so do not attempt to move any of
# the PVE managed interfaces into external files!
auto lo
iface lo inet loopback
iface enp1s0f0 inet manual
iface enp1s0f1 inet manual
auto bond0
iface bond0 inet manual
slaves enp1s0f0 enp1s0f1
bond_miimon 100
bond_mond 802.3ad
#auto enp1s0f1
#iface enp1s0f1 inet static
# address 192.168.1.1
# netmask 255.255.255.0
##Clusternet
auto vmbr0
iface vmbr0 inet static
address 192.168.0.117
netmask 255.255.255.0
gateway 192.168.0.1
bridge_ports bond0
bridge_stp off
bridge_fd 0
auto vlan10
iface vlan10 inet manual
vlan_raw_device bond0
auto vmbr2
iface vmbr2 inet static
address 192.168.1.1
netmask 255.255.255.0
network 192.168.1.0
bridge_ports vlan10
bridge_stp off
bridge_fd 0
#post-up ip route add table vlan10 default via 192.168.1.254 dev vmbr2
#post-up ip rule add from 192.168.1.0/24 table vlan10
#post-down ip route del table vlan10 default via 192.168.1.254 dev vmbr2
#post-down ip rule del from 192.168.1.0/24 table vlan10
#clusternet
auto vlan200
iface vlan200 inet manual
vlan_raw_device bond0
auto vmbr1
iface vmbr1 inet static
address 192.168.200.254
netmask 255.255.255.0
bridge_ports vlan200
bridge_stp off
bridge_fd 0
#post-up ip route add table vlan200 default via 192.168.200.1 dev vmbr2
#post-up ip rule add from 192.168.200.0/24 table vlan200
#post-down ip route del table vlan200 default via 192.168.200.1 dev vmbr2
#post-down ip rule del from 192.168.200.0/24 table vlan200
#storagenet
auto vlan30
iface vlan30 inet manual
vlan_raw_device bond0
auto vmbr30
iface vmbr30 inet static
address 192.168.30.1
netmask 255.255.255.0
network 192.168.30.0
bridge_ports vlan30
bridge_stp off
bridge_fd 0
#post-up ip route add table vlan30 default via 192.168.30.254 dev vmbr30
#post-up ip rule add from 192.168.30.0/24 table vlan30
#post-down ip route del table vlan30 default via 192.168.30.254 dev vmbr30
#post-down ip rule del from 192.168.30.0/24 table vlan30
#VPN
Code:
# network interface settings; autogenerated
# Please do NOT modify this file directly, unless you know what
# you're doing.
#
# If you want to manage part of the network configuration manually,
# please utilize the 'source' or 'source-directory' directives to do
# so.
# PVE will preserve these directives, but will NOT its network
# configuration from sourced files, so do not attempt to move any of
# the PVE managed interfaces into external files!
auto lo
iface lo inet loopback
iface enp3s0 inet manual
#allow-hotplug enp1s0f0
auto enp4s0
iface enp4s0 inet static
address 192.168.1.2
netmask 255.255.255.0
#clusternet
auto enp1s0f2
iface enp1s0f2 inet manual
auto enp1s0f3
iface enp1s0f3 inet manual
auto bond1
iface bond1 inet manual
slaves enp1s0f2 enp1s0f3
bond_miimon 100
bond_mode 802.3ad
auto vmbr1
iface vmbr1 inet static
address 192.168.0.119
netmask 255.255.255.0
gateway 192.168.0.1
bridge_ports bond1
bridge_stp off
bridge_fd 0
#un-vlan 10g bond
auto vlan99
iface vlan99 inet manual
vlan_raw_device bond1
#WANvlan
auto vlan10
iface vlan10 inet manual
vlan_raw_device bond1
#CLUSTERNETvlan
auto vlan30
iface vlan30 inet manual
vlan_raw_device bond1
#VPNvlan
auto vlan50
iface vlan50 inet manual
vlan_raw_device bond1
#PUBLICvlan
auto vlan200
iface vlan200 inet manual
vlan_raw_device bond1
#STORAGENETvlan
auto vmbr0
iface vmbr0 inet static
address 192.168.0.118
netmask 255.255.255.0
gateway 192.168.0.1
bridge_ports enp3s0
bridge_stp off
bridge_fd 0Attachments
-
80.5 KB Views: 41