So, based on a couple posts here, I've managed to configure my ICX-6610 to work with OPNSense...partially.
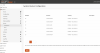
The Brocade is configured as an L3 switch, with OPNSense as it's gateway, similar to this post (OP me), and this post. Switch is 10.100.1.9 (VLAN 1001, management VLAN), 10.199.199.2 (VLAN 999, transit VLAN), OPNSense LAN is 10.199.199.1, laptop is 10.100.1.40 (VLAN 1001, management VLAN). Switch has a default route of 0.0.0.0/0 to 10.199.199.1.
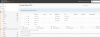
OPNSense has a LAN interface, hooked to the switch (on e 1/2/2) and WAN interface hooked to my ISP. It also has a gateway on the LAN interface pointing to the switch's transit VLAN IP (10.199.199.2). NAT is set to automatic. Static routes for all of my VLANs have been configured to use the gateway.
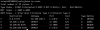
From the switch on VLAN 1001 (management VLAN), I'm able to hit OPNSense at 10.199.199.1 (either by ping or HTTP/S). I can also get to the switch console, and in there I'm able to ping OPNSense.
Beyond that, my laptop has NO internet access. I get the feeling that it's a firewall issue, but I don't really have any rules in place (other than what comes out-of-the-box with OPNSense). My understanding is that the rules, by default, are enough to at least grant internet access, so I'm not sure what I'm missing. I can even see DNS queries going OUT of the LAN interface, and the firewall passes them, but I can't get responses.
Any suggestions?
The Brocade is configured as an L3 switch, with OPNSense as it's gateway, similar to this post (OP me), and this post. Switch is 10.100.1.9 (VLAN 1001, management VLAN), 10.199.199.2 (VLAN 999, transit VLAN), OPNSense LAN is 10.199.199.1, laptop is 10.100.1.40 (VLAN 1001, management VLAN). Switch has a default route of 0.0.0.0/0 to 10.199.199.1.
OPNSense has a LAN interface, hooked to the switch (on e 1/2/2) and WAN interface hooked to my ISP. It also has a gateway on the LAN interface pointing to the switch's transit VLAN IP (10.199.199.2). NAT is set to automatic. Static routes for all of my VLANs have been configured to use the gateway.
From the switch on VLAN 1001 (management VLAN), I'm able to hit OPNSense at 10.199.199.1 (either by ping or HTTP/S). I can also get to the switch console, and in there I'm able to ping OPNSense.
Beyond that, my laptop has NO internet access. I get the feeling that it's a firewall issue, but I don't really have any rules in place (other than what comes out-of-the-box with OPNSense). My understanding is that the rules, by default, are enough to at least grant internet access, so I'm not sure what I'm missing. I can even see DNS queries going OUT of the LAN interface, and the firewall passes them, but I can't get responses.
Any suggestions?