Release notes: omnios-build/ReleaseNotes.md at rn · citrus-it/omnios-build · GitHub
OmniOS "On Monday, Mai 1st OmniOS plans to release OmniOS r151046. There are a bunch of pretty cool new features in the upcoming release, but as it is with cool new features, they also tend to cause regressions. Have a look at the preliminary release notes to get an idea of what is in store (and please let us know if you see any errors or omissions there).
At the moment we are testing the release candidate, and in order to have the best quality release possible, we could really use your help!"
To upgrade to the release candidate use the following package repositories:
OmniOS r151046 (release candidate) (omnios)
OmniOS r151046 extra (extra.omnios)
If you upgrade to the release candidate now, you can later upgrade to the final release.
If you want to try the installation media, you can find them here
Index of /media/r151046/.rc/
The unique selling point of Solaris is the kernelbased SMB server with the following enhancements:
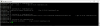
If you look at the output of ls it looks strange for a Unix filer.
The file 1.txt is created locally by root and owner/group is Unix root and the output of ls is as expected
The file 2.txt was created by a Windows client on OmniOS 151046 (both AD members).
ls -l gives gea@local.de (AD user) and ls -n returns the Windows SID of gea@local.de
ls -nn gives the (ephemeral) Unix uid/gid
This is exactly the same info that you get from Windows and Properties > Security > Owner
Why can you see the AD user as owner and not a Unix uid/gid as you would expect on a Unix filesystem like ZFS?
The reason is that the Solaris SMB server use Windows SID directly as an extended ZFS attribute. This gives a worldwide unique user identification as the domain is part of the SID. A Unix uid like 102 is not unique. Even after a backup/restore AD ACL remain intact without any mappings that you need when you use SAMBA instead the Solaris kernelbased SMB .
Udate
If you update to the release candidate, you can later update to the final release
OmniOS "On Monday, Mai 1st OmniOS plans to release OmniOS r151046. There are a bunch of pretty cool new features in the upcoming release, but as it is with cool new features, they also tend to cause regressions. Have a look at the preliminary release notes to get an idea of what is in store (and please let us know if you see any errors or omissions there).
At the moment we are testing the release candidate, and in order to have the best quality release possible, we could really use your help!"
To upgrade to the release candidate use the following package repositories:
OmniOS r151046 (release candidate) (omnios)
OmniOS r151046 extra (extra.omnios)
If you upgrade to the release candidate now, you can later upgrade to the final release.
If you want to try the installation media, you can find them here
Index of /media/r151046/.rc/
The unique selling point of Solaris is the kernelbased SMB server with the following enhancements:
- SMB now supports 256-bit ciphers.
- SMB now has a new configuration option to enable support for short names. Only very old applications on old clients need short names, however it is necessary to support running the Windows Protocol Test Suites.
- ls can show a Domain user or the Windows SID

If you look at the output of ls it looks strange for a Unix filer.
The file 1.txt is created locally by root and owner/group is Unix root and the output of ls is as expected
The file 2.txt was created by a Windows client on OmniOS 151046 (both AD members).
ls -l gives gea@local.de (AD user) and ls -n returns the Windows SID of gea@local.de
ls -nn gives the (ephemeral) Unix uid/gid
This is exactly the same info that you get from Windows and Properties > Security > Owner
Why can you see the AD user as owner and not a Unix uid/gid as you would expect on a Unix filesystem like ZFS?
The reason is that the Solaris SMB server use Windows SID directly as an extended ZFS attribute. This gives a worldwide unique user identification as the domain is part of the SID. A Unix uid like 102 is not unique. Even after a backup/restore AD ACL remain intact without any mappings that you need when you use SAMBA instead the Solaris kernelbased SMB .
Udate
If you update to the release candidate, you can later update to the final release
Last edited:

