The way I've done inter-VLAN routing is using my 100G L3 switch. You could accomplish the same thing with yours. In this config, each VLAN no longer has an interface in the pfSense; instead there is a transit VLAN between pfSense and L3-Switch, with static routes for return packets. Here is roughly what you have to do:
- Goal: Have the pfSense handle internet routing, but your L3 switch handle inter-VLAN routing
- Give your L3 switch an IP on each of your VLAN interfaces. I use 10.41.x.1 for my L3 switch in each VLAN x
- Create a "transit" VLAN that handles routing between the switch and pfSense (I use 10.41.255.1/30)
- Create an interface on pfSense for the transit VLAN, I assigned it 10.41.255.2/30
- Create a default route on the L3 switch pointing to the pfSense IP on the transit VLAN
- Delete/disable all the LAN interfaces on pfSense; the L3 switch will now service those (Keep the Transit, WANs, VPNs, etc)
- Create static routes for all your VLANs, pointing to the the L3 switch transit network's IP (In my case 10.41.255.1)
- Use the DHCP helper feature in the L3 switch to send DHCP requests to a subnet-aware DHCP server (Like Windows Server)
If you can't just break your current setup, you'll need to stage the new infra in parallel then cut it over to maintain service.
Here are some screenshots to help visualize it:
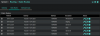
The purpose of the static routes in pfSense is to handle return traffic - When stuff on the internet responds to your local devices, the pfSense needs to know where to send the packets, as the pfSense no longer has interfaces for those subnets - So you put the IP of the L3 switch inside the transit VLAN, where pfSense does have an interface. The transit VLANs are only for routers to pass traffic between each other.
View attachment 28594
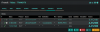
Any firewall rules for devices need to go inside the Transit VLAN, and you can use the Source IP to match which device you want the rule to affect. In my case, I have an alias called "aBrowseThruBoxPN" which specifies certain devices to browse over a VPN instead of my normal WAN. The "Allow All" rule at the bottom allows any device on any VLAN to access the internet. You may not want this. Create Aliases for each VLAN, then use those to control whole subnets.
View attachment 28595
Code:
admin@sonic:~$ show vlan brief
+-----------+----------------+-------------+----------------+-------------+-----------------------+
| VLAN ID | IP Address | Ports | Port Tagging | Proxy ARP | DHCP Helper Address |
+===========+================+=============+================+=============+=======================+
| 50 | 10.41.255.1/30 | Ethernet0 | tagged | disabled | |
| | | Ethernet4 | tagged | | |
| | | Ethernet8 | tagged | | |
| | | Ethernet16 | tagged | | |
| | | Ethernet36 | tagged | | |
+-----------+----------------+-------------+----------------+-------------+-----------------------+
| 102 | | Ethernet0 | tagged | disabled | |
| | | Ethernet4 | tagged | | |
| | | Ethernet8 | tagged | | |
| | | Ethernet16 | tagged | | |
| | | Ethernet36 | tagged | | |
| | | Ethernet112 | untagged | | |
+-----------+----------------+-------------+----------------+-------------+-----------------------+
| 107 | 192.168.7.4/24 | Ethernet0 | tagged | disabled | |
| | | Ethernet4 | tagged | | |
| | | Ethernet8 | tagged | | |
| | | Ethernet16 | tagged | | |
| | | Ethernet36 | tagged | | |
+-----------+----------------+-------------+----------------+-------------+-----------------------+
| 1000 | 10.41.0.1/24 | Ethernet0 | tagged | disabled | 10.41.2.20 |
| | | Ethernet4 | tagged | | 10.41.2.21 |
| | | Ethernet8 | tagged | | |
| | | Ethernet16 | tagged | | |
| | | Ethernet36 | tagged | | |
+-----------+----------------+-------------+----------------+-------------+-----------------------+
| 1001 | 10.41.1.1/24 | Ethernet0 | tagged | disabled | 10.41.2.20 |
| | | Ethernet4 | tagged | | 10.41.2.21 |
| | | Ethernet8 | tagged | | |
| | | Ethernet16 | tagged | | |
| | | Ethernet32 | untagged | | |
| | | Ethernet36 | tagged | | |
| | | Ethernet88 | untagged | | |
| | | Ethernet116 | untagged | | |
| | | Ethernet120 | untagged | | |
| | | Ethernet124 | untagged | | |
+-----------+----------------+-------------+----------------+-------------+-----------------------+
| 1002 | 10.41.2.1/24 | Ethernet0 | tagged | disabled | 10.41.2.20 |
| | | Ethernet4 | tagged | | 10.41.2.21 |
| | | Ethernet8 | tagged | | |
| | | Ethernet16 | tagged | | |
| | | Ethernet36 | tagged | | |
| | | Ethernet38 | untagged | | |
+-----------+----------------+-------------+----------------+-------------+-----------------------+
| 1003 | 10.41.3.1/24 | Ethernet0 | tagged | disabled | 10.41.2.20 |
| | | Ethernet4 | tagged | | 10.41.2.21 |
| | | Ethernet8 | tagged | | |
| | | Ethernet16 | tagged | | |
| | | Ethernet36 | tagged | | |
+-----------+----------------+-------------+----------------+-------------+-----------------------+
| 1008 | 10.41.8.1/24 | Ethernet0 | tagged | disabled | 10.41.2.20 |
| | | Ethernet4 | tagged | | 10.41.2.21 |
| | | Ethernet8 | tagged | | |
| | | Ethernet16 | tagged | | |
| | | Ethernet35 | tagged | | |
| | | Ethernet36 | tagged | | |
+-----------+----------------+-------------+----------------+-------------+-----------------------+
| 1009 | 10.41.9.1/24 | Ethernet0 | tagged | disabled | 10.41.2.20 |
| | | Ethernet4 | tagged | | 10.41.2.21 |
| | | Ethernet8 | tagged | | |
| | | Ethernet16 | tagged | | |
| | | Ethernet36 | tagged | | |
+-----------+----------------+-------------+----------------+-------------+-----------------------+
The L3 switch holds IPs in the VLANs, usually as *.1.
Code:
admin@sonic:~$ show ip int
Interface Master IPv4 address/mask Admin/Oper BGP Neighbor Neighbor IP
----------- -------- ------------------- ------------ -------------- -------------
Loopback0 10.1.0.1/32 up/up N/A N/A
Vlan50 Vrf_Prod 10.41.255.1/30 up/up N/A N/A
Vlan107 Vrf_Prod 192.168.7.4/24 up/up N/A N/A
Vlan1000 Vrf_Prod 10.41.0.1/24 up/up N/A N/A
Vlan1001 Vrf_Prod 10.41.1.1/24 up/up N/A N/A
Vlan1002 Vrf_Prod 10.41.2.1/24 up/up N/A N/A
Vlan1003 Vrf_Prod 10.41.3.1/24 up/up N/A N/A
Vlan1008 Vrf_Prod 10.41.8.1/24 up/up N/A N/A
Vlan1009 Vrf_Prod 10.41.9.1/24 up/up N/A N/A
docker0 240.127.1.1/24 up/down N/A N/A
eth0 192.168.7.2/24 up/down N/A N/A
lo 127.0.0.1/16 up/up N/A N/A
Here you can see the static route on the L3 switch pointing to pfSense at the other end of the transit VLAN. The other routes permit inter-VLAN traffic to pass. The routes in VRF default are to allow the DHCP helper traffic to pass into the Servers VLAN.
Code:
admin@sonic:~$ show ip route vrf all
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
VRF Vrf_Prod:
S>* 0.0.0.0/0 [1/0] via 10.41.255.2, Vlan50, weight 1, 01w3d22h
C>* 10.41.0.0/24 is directly connected, Vlan1000, 01w3d22h
C>* 10.41.1.0/24 is directly connected, Vlan1001, 01w3d22h
C>* 10.41.2.0/24 is directly connected, Vlan1002, 01w3d22h
C>* 10.41.3.0/24 is directly connected, Vlan1003, 01w3d22h
C>* 10.41.8.0/24 is directly connected, Vlan1008, 01w3d22h
C>* 10.41.9.0/24 is directly connected, Vlan1009, 01w3d22h
C>* 10.41.255.0/30 is directly connected, Vlan50, 01w3d22h
C>* 192.168.7.0/24 is directly connected, Vlan107, 01w3d22h
VRF default:
C>* 10.1.0.1/32 is directly connected, Loopback0, 01w3d22h
S>* 10.41.2.0/24 [1/0] is directly connected, Vlan1002 (vrf Vrf_Prod), weight 1, 01w3d22h
S>* 10.41.3.0/24 [1/0] is directly connected, Vlan1003 (vrf Vrf_Prod), weight 1, 01w3d22h
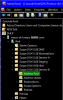
You'll need a subnet-aware DHCP server. Since I run AD I use MS DHCP (and DNS as well). You setup a scope for each VLAN with the desired IP range, domain suffix, etc.
View attachment 28596
Hopefully that gives a starting point. A "Hybrid" approach is also possible where both the L3 switch and pfSense act as a router for all VLANs. This allows you to keep using pfSense for DHCP. I don't like this option, because then you have 2 routers per VLAN doing asymmetric routing, and it causes all sorts of undesirable issues.
It's way better to use the enterprise-ish method of a subnet-aware multi-scope DHCP service and a small transit vlan between routers.