There are no aliases that I know of in the switch ACLs.
Here's an example you should be able to work from. This is from 8.0.30 firmware not sure if it's the same on 7xxx series firmware.
Code:
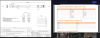
ip access-list extended guest-v4
remark DENY ADMIN ACCESS TO SWITCH
deny tcp any host 10.23.15.1 eq ssh log
deny tcp any host 10.23.15.1 eq telnet log
deny tcp any host 10.23.15.1 eq http log
deny tcp any host 10.23.15.1 eq ssl log
remark ALLOW SAME VLAN TRAFFIC
permit ip any 10.23.15.0 0.0.0.255
remark ALLOW DHCP
permit udp any any eq bootps
permit udp any any eq bootpc
remark ALLOW ICMP
permit icmp any any
remark ALLOW ESTABLISHED TCP TRAFFIC
permit tcp any any established
remark ALLOW DNS REQUESTS
permit udp any host 10.23.60.3 eq dns
permit tcp any host 10.23.60.3 eq dns
permit udp any host 10.23.60.5 eq dns
permit tcp any host 10.23.60.5 eq dns
remark ALLOW ACCESS TO CACHE01 HTTP/S
permit tcp any host 10.23.60.5 eq http
permit tcp any host 10.23.60.5 eq ssl
remark ALLOW RETURN OF SNMP TRAFFIC TO MON01
permit udp any eq snmp host 10.23.60.81
permit udp any eq snmp-trap host 10.23.60.81
remark DENY ALL OTHER INTER-VLAN TRAFFIC
deny ip any 10.0.0.0 0.255.255.255 log
remark PERMIT REMAINING TRAFFIC
permit ip any any
enable-accounting
In the above example, you will see same-VLAN traffic is permitted while other VLAN traffic can not be sent with a few exceptions (already established TCP from another VLAN, some specific TCP/UDP traffic (remember UDP traffic is never "established"). After being denied access to other VLANs (less the specific allows), all traffic is permitted (to the internet).