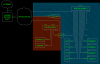
I have an ISP provided cable modem/router combo (Hitron from ~2012) that I cannot get to bypass the router part. Because of this, I'm having issues separating my work network from my not-work networks. In a perfect world, I have 2x wifi networks ([2] guest/smart devices/random {phones, etc.}, [3] work), and 2x wired networks ([3] guest/smart devices, [2] work).
I know my APs can do VLAN tagging, but the ISP router can't interpret that. I also want the NAS to be accessible from both networks (its 2x NICs can be run as separate networks); if things work how I think, there is no two routes to the NAS from any device. I tried making a guest network on my AP, but then devices can't connect to each other within that network, and that stops many of my smart devices from working together.
I'm not really looking for a how to, but moreso what hardware I'm looking at needing to accomplish this to get me started. It feels like I can maybe do this with my Mikrotik, but I would need everything on port 1 to "become" VLAN 1 (switch connected with relevant devices), port 2 to "become" VLAN 2 (switch connected with relevant devices), then port 3 to be routed to whatever VLAN it is tagged by the AP. Everyone can access port 4 (Internet). My Internet is 40/10.
I have in my possession:
1x Hitron modem/router combo (this cannot be changed)
1x Mikrotik Hex Lite (this used to be my router)
3x Unifi WiFi 6 APs
1x "managed" 8 port switch (NetGear GS108PE)
1x unmanaged 16 port switch
1x unmanaged 6 port 10gbe/2.5gbe switch
1x Hubitat home hub (wired)
1x Hue hub (wired)
1x Misc.smart home stuff (wireless)
1x VoIP device (wired)
1x NAS (wired x2 ... file server, camera server)
1x work PC (wired)
1x work laptop (wireless)
1x server (wired ... FTP, WWW, VPN, Plex, etc.)
Currently, everything is on the same network, which I am not in love with. Hopefully my pic makes sense for what I want to do. I'm OK with having to access the NAS my IP.
I know my APs can do VLAN tagging, but the ISP router can't interpret that. I also want the NAS to be accessible from both networks (its 2x NICs can be run as separate networks); if things work how I think, there is no two routes to the NAS from any device. I tried making a guest network on my AP, but then devices can't connect to each other within that network, and that stops many of my smart devices from working together.
I'm not really looking for a how to, but moreso what hardware I'm looking at needing to accomplish this to get me started. It feels like I can maybe do this with my Mikrotik, but I would need everything on port 1 to "become" VLAN 1 (switch connected with relevant devices), port 2 to "become" VLAN 2 (switch connected with relevant devices), then port 3 to be routed to whatever VLAN it is tagged by the AP. Everyone can access port 4 (Internet). My Internet is 40/10.
I have in my possession:
1x Hitron modem/router combo (this cannot be changed)
1x Mikrotik Hex Lite (this used to be my router)
3x Unifi WiFi 6 APs
1x "managed" 8 port switch (NetGear GS108PE)
1x unmanaged 16 port switch
1x unmanaged 6 port 10gbe/2.5gbe switch
1x Hubitat home hub (wired)
1x Hue hub (wired)
1x Misc.smart home stuff (wireless)
1x VoIP device (wired)
1x NAS (wired x2 ... file server, camera server)
1x work PC (wired)
1x work laptop (wireless)
1x server (wired ... FTP, WWW, VPN, Plex, etc.)
Currently, everything is on the same network, which I am not in love with. Hopefully my pic makes sense for what I want to do. I'm OK with having to access the NAS my IP.
Attachments
-
574.2 KB Views: 13
Last edited: