ISP provides one IP address / single port on modem. Adding a switch upstream of firewall seems handy for testing ISP connection, playing around without disturbing main network etc From my searching this is common practice (failover/two ISP/HA) but I'm not finding any guides and I'm curious how it works.
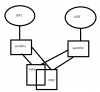
Basic 5 port switch seems common but I think it has to be more than just vlan aware.
Obviously lock down management vlan/port (say vlan 10, port 5, could add IP/other restrictions)
ISP modem on port 1
Switch in DHCP mode so it gets IP/Gateway from modem (ie 174.xxx.xxx.90/174.xxx.xxx.xxx.1) and modem stays happy seeing only one MAC
.... Then what ????
firewall/router A on port 2
firewall/router B on port 3
Ports 1-3 PVID and untagged on vlan 20?
It seems at this point there has to be some sort of NAT or routing configured right? I'm playing with netgear GS108T for reference.
Thanks!
Basic 5 port switch seems common but I think it has to be more than just vlan aware.
Obviously lock down management vlan/port (say vlan 10, port 5, could add IP/other restrictions)
ISP modem on port 1
Switch in DHCP mode so it gets IP/Gateway from modem (ie 174.xxx.xxx.90/174.xxx.xxx.xxx.1) and modem stays happy seeing only one MAC
.... Then what ????
firewall/router A on port 2
firewall/router B on port 3
Ports 1-3 PVID and untagged on vlan 20?
It seems at this point there has to be some sort of NAT or routing configured right? I'm playing with netgear GS108T for reference.
Thanks!