I recently setup a new network on the other side of the country and before I left, I managed to get my USG up and running but my problem now is that my network isn't configured correctly and I can't get the VPN to work right.
I have a feeling my issue is with Routes/ Subnets/ Subnet Masks.
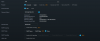
My USG is running into a Fortinet Fortigate and I have an External IP assigned to my port of 71.14.xxx.xxx.
My gateway IP is 192.168.150.1 and my WAN address is 192.168.150.5 (supposedly set-up by people smarter than I).
I was then told (again by people assumed to be smarter than I) that I can't talk to my device because my USG was giving itself an internal LAN IP of 192.168.1.1 so I went in and changed the "Gateway/Subnet" setting on the Network page so that it was 192.168.150.1/24 to match what I'm supposed to be in according to the Fortigate but that didn't have the desired effect either.
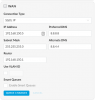
At the end of the day, I need my USG to think its address is really 71.14.xxx.xxx (which is where all packets get forwarded that hit the WAN IP anyways) and then to have an internal LAN that I can bridge to through the L2TP VPN.
OR
My issue is with the person who set up the Fortigate because I can't even ping my USG, which I believe means that my packets aren't getting forwarded as well as they should be.
Does anyone have any suggestions, or see pretty easily where I went wrong?
I have a feeling my issue is with Routes/ Subnets/ Subnet Masks.
My USG is running into a Fortinet Fortigate and I have an External IP assigned to my port of 71.14.xxx.xxx.
My gateway IP is 192.168.150.1 and my WAN address is 192.168.150.5 (supposedly set-up by people smarter than I).
I was then told (again by people assumed to be smarter than I) that I can't talk to my device because my USG was giving itself an internal LAN IP of 192.168.1.1 so I went in and changed the "Gateway/Subnet" setting on the Network page so that it was 192.168.150.1/24 to match what I'm supposed to be in according to the Fortigate but that didn't have the desired effect either.
At the end of the day, I need my USG to think its address is really 71.14.xxx.xxx (which is where all packets get forwarded that hit the WAN IP anyways) and then to have an internal LAN that I can bridge to through the L2TP VPN.
OR
My issue is with the person who set up the Fortigate because I can't even ping my USG, which I believe means that my packets aren't getting forwarded as well as they should be.
Does anyone have any suggestions, or see pretty easily where I went wrong?
Attachments
-
56.1 KB Views: 15
-
22.2 KB Views: 15
Last edited: