I want to start thinking about the layout of the home network before proceeding with wiring and would like to make sure I'm not making any mistakes.
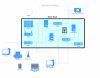
My current plan is to have all of the CAT cables wired to where the rack will be, which should allow me to have whatever network layout I want. I've attached a high level network diagram that shows how I plan to connect all of the components together, but I am not sure if what I have is considered best practice.
1. I want to be able to semi-isolate parts of the network. For instance, home automation devices, and surveillance cameras, etc. However, I still want to be able to access some of these resources remotely via VPN, such as the surveillance recordings. Is it feasible to have the cameras or devices themselves be isolated, but the server managing those devices be accessible over the WAN? Another reason for isolating is to prevent the recording traffic from affecting the main network.
2. Other parts of the network would be isolated completely (IPMI, private file servers). Does the setup in the diagram make sense or am I over-complicating things? I'm not sure how this is normally done. Is VLAN or subnetting a more practical way to accomplish this?
3. Should I go virtual for everything (VLANs, VM's)? I am hesitant because most of this is new to me and I figured it might be easier to learn by starting off with everything physical and virtualize later.
I don't think the platform would affect the layout, but I'm listing it just in case:
- firewall/router: OPNSense
- Managed switches (POE-capable for Wireless AP and IP Cameras)
- PC NVR: Blue Iris
- Home automation: Home Assistant
- File server: TrueNas
- Stream server: Plex
FYI, these are just solutions I've chosen based on my research. I am not set on any of them so please let me know if there are better alternatives.
I haven't completely figured out the home automation yet, but it seems like most devices communicate through mesh network which would have a hub that connects to the home network via ethernet.
My current plan is to have all of the CAT cables wired to where the rack will be, which should allow me to have whatever network layout I want. I've attached a high level network diagram that shows how I plan to connect all of the components together, but I am not sure if what I have is considered best practice.
1. I want to be able to semi-isolate parts of the network. For instance, home automation devices, and surveillance cameras, etc. However, I still want to be able to access some of these resources remotely via VPN, such as the surveillance recordings. Is it feasible to have the cameras or devices themselves be isolated, but the server managing those devices be accessible over the WAN? Another reason for isolating is to prevent the recording traffic from affecting the main network.
2. Other parts of the network would be isolated completely (IPMI, private file servers). Does the setup in the diagram make sense or am I over-complicating things? I'm not sure how this is normally done. Is VLAN or subnetting a more practical way to accomplish this?
3. Should I go virtual for everything (VLANs, VM's)? I am hesitant because most of this is new to me and I figured it might be easier to learn by starting off with everything physical and virtualize later.
I don't think the platform would affect the layout, but I'm listing it just in case:
- firewall/router: OPNSense
- Managed switches (POE-capable for Wireless AP and IP Cameras)
- PC NVR: Blue Iris
- Home automation: Home Assistant
- File server: TrueNas
- Stream server: Plex
FYI, these are just solutions I've chosen based on my research. I am not set on any of them so please let me know if there are better alternatives.
I haven't completely figured out the home automation yet, but it seems like most devices communicate through mesh network which would have a hub that connects to the home network via ethernet.
Attachments
-
474.7 KB Views: 70