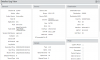
I posted this on reddit and figured I would share here too because I think it's hilarious.
So for my day job I am in charge if a relatively large enterprise with about 30,000 total users.
For Firewall on the edge we have had both Fortigate and now Palo Alto. For everything else, we have been using pfSense. All of my Guest and BYOD Network traffic terminate through CAPWAP tunnels behind pfSense firewalls with either a captive portal or a 802.x auth. I also use it for some site-to-site, HA Proxy and some other internal security stuff. Big fan
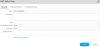
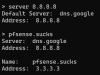
Anyway, about a year ago I put a policy on the BYOD network similar to this one: Your Smart TV is probably ignoring your PiHole - LabZillaWhereby users who think they are clever and want to bypass DNS filtering are basically stopped in their tracks. I find it hilarious because they don't even know how or why the filter is still working because the device thinks Google or Cloudflare or whatever is telling them that the IP of website they are trying to go to is a blockpage on my network > .
.
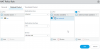
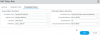
In any case, I asked my Palo Rep how I could do something similar in my production network because I was having trouble getting the NAT rules to commit. Apparently, they can't and he was just as floored as I was. When you write dNAT rules you can't have more than one destination (in other words you can't use "any" destination in the "untrusted" zone or WAN, it has to be a 1:1 mapping). In their own support community, apparently someone else tried to do this 10 years ago and they still haven't added this feature in. Their official stance is just block outgoing traffic to port 53 from devices that aren't authorized DNS servers.
Now, I love my Palo Alto and I have absolutely no intentions of dumping it in favor of pfSense for the job its doing. I honestly don't think I could handle the routing, let alone the fact I would lose alot of functionality in the Layer 7 side of the house and a whole host of other things...Enterprise products are for Enterprise for a reason
However, I just have to say - score one for the Open Source community lol!
So for my day job I am in charge if a relatively large enterprise with about 30,000 total users.
For Firewall on the edge we have had both Fortigate and now Palo Alto. For everything else, we have been using pfSense. All of my Guest and BYOD Network traffic terminate through CAPWAP tunnels behind pfSense firewalls with either a captive portal or a 802.x auth. I also use it for some site-to-site, HA Proxy and some other internal security stuff. Big fan
Anyway, about a year ago I put a policy on the BYOD network similar to this one: Your Smart TV is probably ignoring your PiHole - LabZillaWhereby users who think they are clever and want to bypass DNS filtering are basically stopped in their tracks. I find it hilarious because they don't even know how or why the filter is still working because the device thinks Google or Cloudflare or whatever is telling them that the IP of website they are trying to go to is a blockpage on my network >
In any case, I asked my Palo Rep how I could do something similar in my production network because I was having trouble getting the NAT rules to commit. Apparently, they can't and he was just as floored as I was. When you write dNAT rules you can't have more than one destination (in other words you can't use "any" destination in the "untrusted" zone or WAN, it has to be a 1:1 mapping). In their own support community, apparently someone else tried to do this 10 years ago and they still haven't added this feature in. Their official stance is just block outgoing traffic to port 53 from devices that aren't authorized DNS servers.
Now, I love my Palo Alto and I have absolutely no intentions of dumping it in favor of pfSense for the job its doing. I honestly don't think I could handle the routing, let alone the fact I would lose alot of functionality in the Layer 7 side of the house and a whole host of other things...Enterprise products are for Enterprise for a reason
However, I just have to say - score one for the Open Source community lol!