I've been thinking of replacing my current debian router with gentoo router and while I'm doing it I might as well document all of it. Gentoo install script, firewall rules generated by ferm, kernel configs, bird config, various /etc/ configs, scripts and fail proofing scripts for the the router (eg, cannot generate ferm rules if wan interface hasn't gotten ip from dhcp).
Why would I want to document everything publicly? To share ideas and possibly catch some from more experienced network/sys admins.
So any takers?
Going to fire up the test VM this weekend and look into the install script and kernel configs. After the test vm is up and running I'll just run the install script and drop in configs and it'll be done.
Rough software stack:
- kernel 4.4.1
- ferm
- bird
- isc-dhcp
Hardware:
- i3-3220T
- 8G ECC
- 32GB SLC SSD
- 4x gig intel nic
- 2x 10gig br1020 nic
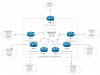
Network topology:
- wan: get ip from ISP and nat 2 lan vlans
- lan: 3-4 lan vlans and 1 ovpn network
Why would I want to document everything publicly? To share ideas and possibly catch some from more experienced network/sys admins.
So any takers?
Going to fire up the test VM this weekend and look into the install script and kernel configs. After the test vm is up and running I'll just run the install script and drop in configs and it'll be done.
Rough software stack:
- kernel 4.4.1
- ferm
- bird
- isc-dhcp
Hardware:
- i3-3220T
- 8G ECC
- 32GB SLC SSD
- 4x gig intel nic
- 2x 10gig br1020 nic
Network topology:
- wan: get ip from ISP and nat 2 lan vlans
- lan: 3-4 lan vlans and 1 ovpn network